What is MITRE:
It’s a non-profitable organization, founded in 1958, works to do research on different cyberattacks, study them, find out steps involve in that attack, prepare plan to avoid such attacks in future & document all these things on their knowledge base to help government, private sectors, financial & health sectors to keep updated and secure.
Everyone can access their knowledge base, to understand what all types of attacks are there, what are steps involved in each type of attack and how we can keep our organization protected from such attacks.
They work closely with U.S. government agencies to solve critical challenges. For example, they might help the military develop new technologies or improve public health systems.
MITRE conducts research and creates advanced technologies to address complex problems. They have special projects called “federally funded research and development centers” (FFRDCs) where they innovate in areas like cybersecurity, aviation safety, and healthcare. In cybersecurity, MITRE is known for creating tools and frameworks that help organizations understand and defend against cyber threats. One famous tool is the MITRE ATT&CK framework, which maps out the tactics and techniques used by cyber attackers.
MITRE ATT&CK Framework:
MITRE created ATT&CK framework in 2019, has details about all types of attacks, tactics & techniques used in that attack.
Tactics: You can consider tactics as an aim of threat actor, what is their aim in specific attack?
Techniques: It’s a procedure or method used to achieve above aim/tactics.
ATT&CK: Stands for Adversary Tactics, Techniques & Common Knowledge
Adversary is another word for hackers, attackers, threat actors, enemy, opponent or competitor of the cybersecurity team.
According to MITRE ATT&CK Framework, below are the common series of tactics attackers plan and execute using different underlying techniques:
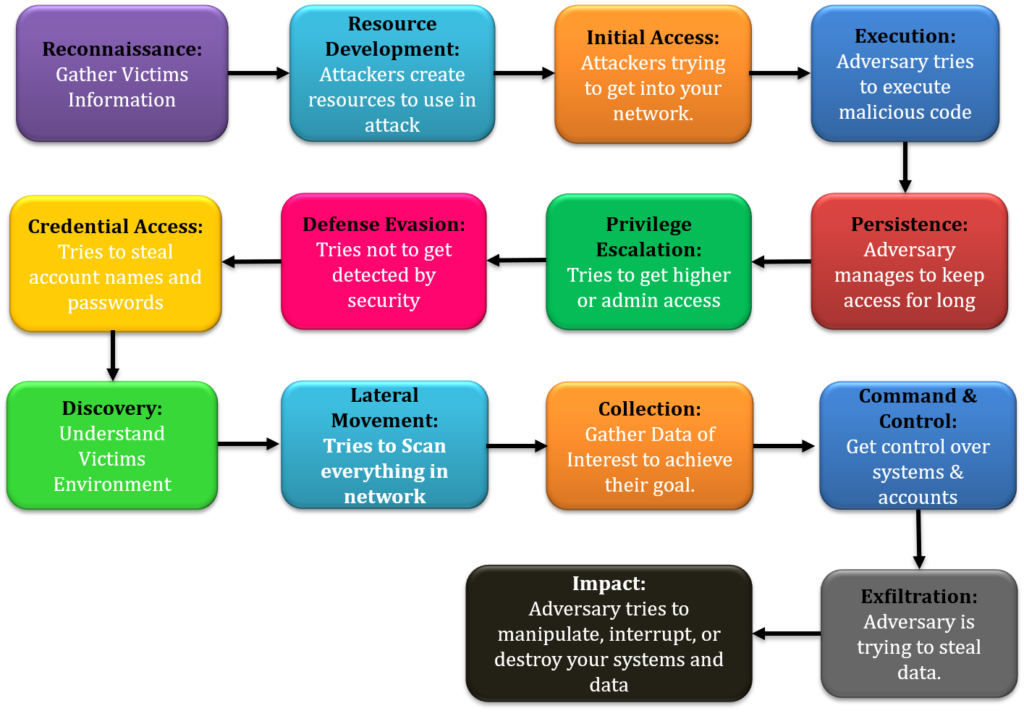
Each of the above tactics has multiple techniques defined in it to accomplish that respective tactic.
Use of MITRE ATT&CK Framework:
Threat Detection:
SOC team uses this framework to understand and identify adversary behavior within environment by mapping detected activities with ATT&CK tactics & techniques.
They will able to predict the potential impact happen or they may able to control series of tactics at early stage.
e.g: If SOC team find out malicious links in email, then they can aware users regarding that Phishing technique used and can control execution tactic followed by other tactics in series.
Threat Intelligence:
Threat Intelligence will give idea about emerging threat actors, tactics & techniques they use in specific attack and how we can protect our organization or environment from that type of attack.
e.g. from above email phishing example, threat intelligence feeds will publish those malicious links and it will also have details about tactics & techniques used in that specific phishing attack. By referring to MITRE ATT&CK framework, SOC team will identify techniques used and then plan to mitigate those attacks by blocking those malicious links at security system.
Run Adversary Emulation Plans:
Red teams and penetration testers use ATT&CK to simulate real-world cyber-attacks. By emulating the behavior of known adversaries, they can test the effectiveness of an organization’s defenses and identify weaknesses. Red Team can develop and deploy a consistent and highly organized approach to defining the tactics and techniques of specific threats, then logically assess their environment to see if the defenses work as expected.
Security Gaps Assessment:
By running above emulation, Blue team will know where are the gaps in their environment. What type of policies they need to put in, what type of firewall rules they have to ask security operations team to implement. What type of threat hunts they need to carry out in their environment. ATT&CK metrics can help here to understand suggested remedies and compensating control techniques to fill those gaps and improve overall security posture of the environment.
Thanks for giving such critical information in simple way..
Very well written article. It will be supportive to everyone who employess it, as well as me. Keep up the good work – looking forward to more posts.
obviously like your web-site however you need to test the spelling on several of your posts. Several of them are rife with spelling problems and I to find it very bothersome to tell the truth on the other hand I will definitely come again again.