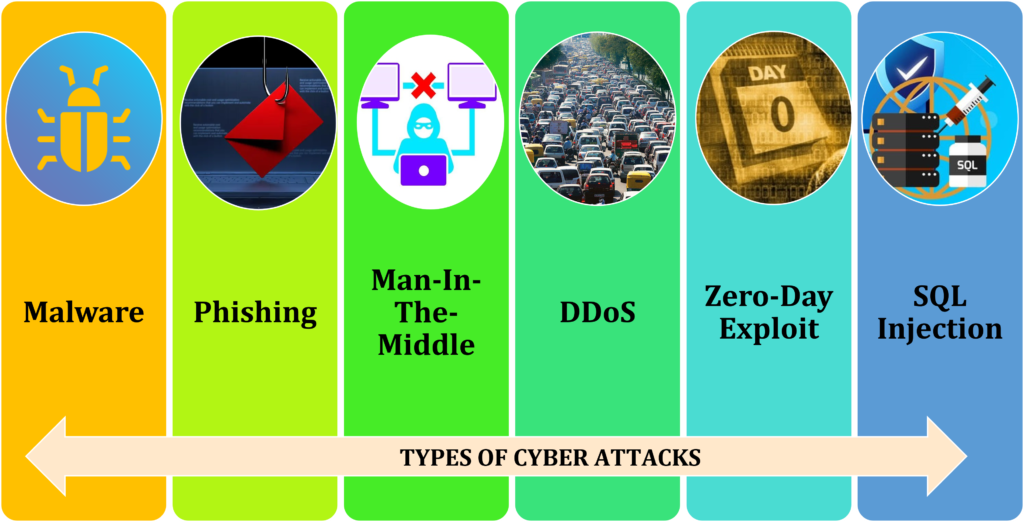
Types of Cyber Attacks:
Malware:
Malware is a software which is malicious, includes spyware, ransomware, viruses, Trojan
Horses and worms. Malware can break and gain access to network or system through vulnerability whenever user install that malicious software by clicking on external, dangerous, and untrusted links or email attachments.
Terms explanation:
Software: Program use to perform specific task in your system/computer or network.
Spyware: It is a type of software that installs itself on a device and secretly monitors a user/victim’s or system owner online activity.
Ransomware: It a type of software designed to block access to computer/system or some files on system and demands a payment to enable access again and successful payment can lead to financial loss.
Virus: It is a malicious software program loaded onto a user’s computer without the user’s knowledge and performs malicious actions.
Trojan Horse: it is a type of malicious code or software that looks legitimate but can take control of your computer.
Worms: It is a malicious software that can replicate itself rapidly and spread across devices within a network without user/victim’s interaction.
Vulnerability: It is a bug, weakness, flaw or error found in computer systems/server or networks that can exploited by hackers.
Phishing:
Cybercriminals targets individuals or organizations by sending them email, text messages,
popup messages, phone calls, and may use other social forms of communication. Message will contain links or attachments which can steal sensitive data like credit cards and login information by clicking on it, or to install malware software on targeted victim’s system. The source of mail sender sometime appears very reputable and trusted.
Man-In-The-Middle (MitM):
As per its name cybercriminals sit in the middle of network and computers, handset devices,
card scanning machines etc. Attackers insert themselves between the communicating channels by Wi-Fi Eavesdropping, Packet Sniffing, DNS Spoofing, SSL Stripping, Email Hijacking, ARP Spoofing to interrupt traffic and steal data.
Terms explanation:
Wi-Fi Eavesdropping: On public insecure Wi-Fi, attackers can insert themselves between network and devices connected to that Wi-Fi network. All activities over that Wi-Fi network can
pass through attackers. Attackers can steal all user personal, professional,
and financial information by sitting in middle.
Packet Sniffing: Attackers can use different packet sniffers application which can capture data packets across computer and networks. Data packets can have login credentials, credit/debit,
or account login details.
DNS Spoofing:
Attackers can alter IP Address details available at Domain Name System to redirect users to malicious websites by providing incorrect IPAddress for standard websites.
SSL Striping: Attackers will be between web client and web server. Attackers may attempt to
downgrade the secure connection to decrypted HTTP connection.
Email Hijacking: Attackers compromises and gain access to victim’s email account and then silently monitor the communications between client and provider.
ARP Spoofing: Address Resolution Protocol (ARP) spoofing involves manipulating ARP tables, in which hacker sends fake APR packets that has attackers MAC address link with an IP Address of computer connected over LAN. Attackers can steal the data communicated between devices over LAN.
Denial-of-service (DoS):
Cybercriminals attempts to malfunction system, service, or network by flooding it with
illegitimate traffic or requests to exhaust resources and bandwidth. Which is result make system unavailable for intended users so that system won’t allow access to legitimate users also called as Denial of service. This is also known as distributed-denial-of-service (DDoS) attack or Bonet attack.
Terms explanation:
Bonet: A Bonet is a collection of devices connected with network, which are attacked, infected and controlled by cybercriminals.
Zero-Day Exploit:
When software developers release software without realizing that their software has flaw/vulnerability and as software is released, they have 0 days to fix that vulnerability. And professional and aware cybercriminals use that flaw to hack the software before a patch or solution is implemented. It typically includes various types of software, including operating systems, web browsers and applications.
Terms explanation:
Patch: It’s a piece of code that is designed to fix, update, or improve a program or to fix errors, bugs, flaws, and vulnerabilities.
SQL injection:
Cybercriminals create new or manipulate existing structured query which they will insert into server to gain unauthorized access to a database which can expose intellectual property, customer data or administrative credentials of business.
Terms explanation:
SQL: Structured Query Language includes set of parameters which matches with columns of table in database.
Database: It’s a software used to manage and store data in the form of tables. Each table contains row & columns.
I抦 impressed, I have to say. Really rarely do I encounter a weblog that抯 both educative and entertaining, and let me inform you, you might have hit the nail on the head. Your idea is outstanding; the problem is something that not enough individuals are speaking intelligently about. I’m very pleased that I stumbled throughout this in my seek for something referring to this.
Thanks for your feedback.
I know this if off topic but I’m looking into starting my own blog and was curious what all is needed to get set up? I’m assuming having a blog like yours would cost a pretty penny? I’m not very internet savvy so I’m not 100 positive. Any tips or advice would be greatly appreciated. Appreciate it
Hi,
I am also new in blogging, but I have spent around 4500 for 1 year hosting with domain.
Hostinger is the platform I have chosen, and I am still trying to setup my blog website through youtube videos using wordpress.
What i do not realize is actually how you’re not actually much more well-liked than you might be now. You’re very intelligent. You realize thus significantly relating to this subject, made me personally consider it from numerous varied angles. Always maintain it up!
This is really interesting, You’re a very skilled blogger. I have joined your feed and look forward to seeking more of your magnificent post. Also, I’ve shared your site in my social networks!
Thank you for the sensible critique. Me & my neighbor were just preparing to do a little research about this. We got a grab a book from our local library but I think I learned more from this post. I’m very glad to see such excellent information being shared freely out there.
I have learned new things through your web site.
Thanks
I do agree with all of the ideas you have presented in your post. They’re very convincing and will definitely work. Still, the posts are too short for newbies. Could you please extend them a bit from next time? Thanks for the post.
Sure, Will consider it from next time.
I love your blog.. very nice colors & theme. Did you make this website yourself or did you hire someone to do it for you? Plz answer back as I’m looking to design my own blog and would like to find out where u got this from. thanks a lot
I manage it, I have used Sparkling theme of WordPress.
Hello! Do you know if they make any plugins to safeguard against hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any recommendations?
Please take a look at this blog post, you may get some idea.
https://www.hostinger.in/tutorials/downloading-website-backup
You made some nice points there. I looked on the internet for the issue and found most guys will go along with with your website.
This is really attention-grabbing, You’re an overly skilled blogger. I’ve joined your rss feed and sit up for in search of more of your wonderful post. Additionally, I have shared your web site in my social networks!
Hi would you mind letting me know which webhost you’re working with? I’ve loaded your blog in 3 completely different web browsers and I must say this blog loads a lot faster then most. Can you recommend a good internet hosting provider at a honest price? Cheers, I appreciate it!
Hi,
I am using Hostinger premium web hosting.
Nice post. I was checking continuously this blog and I am impressed! Very useful info specifically the ultimate part 🙂 I take care of such information a lot. I used to be looking for this particular information for a long time. Thank you and good luck.
Whats up this is somewhat of off topic but I was wanting to know if blogs use WYSIWYG editors or if you have to manually code with HTML. I’m starting a blog soon but have no coding knowledge so I wanted to get advice from someone with experience. Any help would be enormously appreciated!
You don’t have to write HTML code for any blog post. WordPress has ability and it allows you to write post in the blocks.
Add required blocks and write in them. e.g. heading, paragraph, image etc.
Wow! Thank you! I continually wanted to write on my blog something like that. Can I implement a portion of your post to my blog?
Sure, You can implement it also you can link my website for more information.
Thanks for sharing superb informations. Your website is very cool. I’m impressed by the details that you have on this blog. It reveals how nicely you perceive this subject. Bookmarked this website page, will come back for more articles. You, my pal, ROCK! I found simply the info I already searched all over the place and just couldn’t come across. What an ideal website.
I would like to point out my affection for your kindness supporting those who have the need for help on this important idea. Your special commitment to passing the message up and down ended up being amazingly effective and have all the time enabled some individuals much like me to reach their pursuits. This useful report indicates so much a person like me and additionally to my fellow workers. Thanks a lot; from each one of us.
A person necessarily help to make critically articles I’d state. That is the very first time I frequented your website page and up to now? I surprised with the research you made to make this particular put up incredible. Magnificent task!
Whats Happening i am new to this, I stumbled upon this I’ve found It absolutely helpful and it has aided me out loads. I hope to contribute & aid other users like its helped me. Great job.
Whats up! I just wish to give a huge thumbs up for the nice data you have here on this post. I will likely be coming again to your blog for more soon.
I have read some good stuff here. Certainly worth bookmarking for revisiting. I wonder how much effort you put to create such a magnificent informative website.
Someone necessarily lend a hand to make severely posts I’d state. This is the first time I frequented your web page and so far? I amazed with the analysis you made to make this actual put up incredible. Wonderful activity!
It’s a pity you don’t have a donate button! I’d most certainly donate to this outstanding blog! I suppose for now i’ll settle for book-marking and adding your RSS feed to my Google account. I look forward to new updates and will share this website with my Facebook group. Chat soon!
I like the valuable info you provide in your articles.
I will bookmark your blog and check again here regularly.
I am quite sure I will learn a lot of new stuff right here!
Best of luck for the next!
Yeah bookmaking this wasn’t a risky decision great post! .
I am immediately seize your rss as I can not in finding your e-mail subscription link or newsletter service. Do you have any? Kindly let me realize in order that I may subscribe. Thanks.
Hey I am so thrilled I found your website, I
really found you by mistake, while I was researching on Digg
for something else, Regardless I am here now and would
just like to say cheers for a tremendous post and a all round exciting blog (I also love the theme/design), I don’t have time to
browse it all at the minute but I have bookmarked it and
also added your RSS feeds, so when I have think I will be back to read much more, Please do keep up the excellent.
We absolutely love your blog and find many of your post’s to be exactly I’m looking for.
Does one offer guest writers to writ content
for yourself? I wouldn’t mind creating a post or
elaborating on a lot of the subjects you write with regards to here.
whoah this blog is great i eally like studyig your articles.
Keep upp the good work! You already know, a lot of individuals are hunting round for this information, you could help them greatly.