For any business to operate successfully, it is crucial to handle data with care. To achieve this, every business operation should align with the principles of the CIA triad.
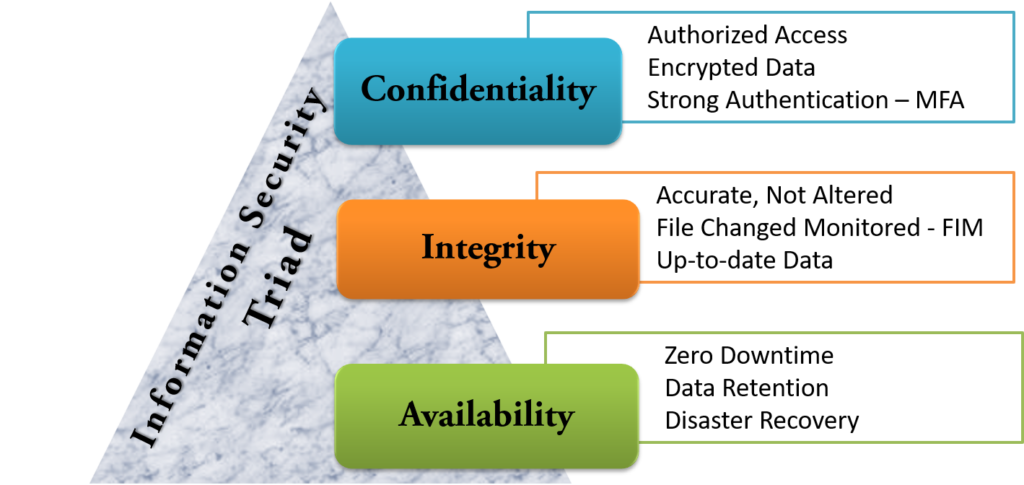
CIA stands for Confidentiality, Integrity, and Availability. Each of these principles plays a vital role in information security. Data must be kept confidential, its integrity must be maintained, and it must be available around the clock, 24/7.
Lets understand CIA Triad in detail:
Confidentiality:
When it comes to ensuring the confidentiality of data, maintaining its security is of paramount importance. Just like we store our important documents in lockers or drawers at home to keep them safe, or deposit our money in banks for protection, we rely on various measures to safeguard sensitive information.
Banks, for example, play a crucial role in protecting personal data. They ensure that account details, balances, and transactions remain confidential. Access to such information is restricted to authorized bank employees and the account holder alone. Furthermore, banks limit access by giving employees only the permissions necessary for their roles. Employees are not allowed to perform any transactions without the account holder’s explicit consent.
A similar level of confidentiality is maintained when it comes to military data, which is considered highly sensitive and is never transmitted in plain text. Instead, it’s encoded in secure formats, as often depicted in movies.
When focusing on data confidentiality, there are several key factors that must be prioritized:
- Authorized Access: Only individuals who are granted permission should have access to sensitive data.
- Limited Access with Least Possible Permissions: Users should be given the minimal permissions necessary to perform their tasks.
- Data Encryption: Sensitive data must be encrypted to prevent unauthorized access.
- Strong Authentication (MFA): Multi-factor authentication (MFA), such as OTP-based authentication, should be implemented to ensure only authorized users can access the data.
By incorporating these principles, organizations can maintain the confidentiality and integrity of sensitive data, protecting it from unauthorized access and potential breaches.
Integrity:
When you enable auto-debit payments from your bank account or cards, you usually don’t worry about whether the money will be transferred to the correct billing account. This is because you trust the service provided by your bank or the payment gateway provider to ensure the payment goes to the right destination, such as the correct account number, UPI ID, or payment gateway. This trust is built on the integrity of the information. If attackers were able to change the payment destination, it would result in financial loss, and you would lose trust in the service provider. Therefore, maintaining data integrity is crucial to keeping information safe, accurate, and reliable.
To maintain the integrity of data, the following aspects are given priority:
- Data Accuracy: The data must be correct and not altered in any way.
- File Changes Are Monitored: File Integrity Monitoring (FIM) is used to detect any changes to critical files.
- Data Should Be Up-to-Date: Information must be regularly updated to ensure it remains current and accurate.
By focusing on these key aspects, organizations can ensure their data remains secure, trustworthy, and accurate, providing confidence to their users.
Availability:
Imagine you need to make an emergency transaction, but what if your bank’s portal or app isn’t working? If the service is unavailable when you need it most, it can be incredibly frustrating. You might even consider closing your account with that bank, which results in a potential loss of a customer for the bank. Additionally, if you can’t access your old transaction statements, it means the bank is not retaining essential transaction data as required. This illustrates the importance of availability in data and services.
Similarly, consider browsing products on an e-commerce website, but the site is loading slowly or not loading at all. If it takes more than a few minutes to load, you’ll likely switch to another website and make a purchase there instead. This can result in thousands of potential customers taking similar actions, causing significant financial losses for the company.
This emphasizes why data availability is crucial for any business.
To maintain the availability of data, the following factors are prioritized:
- Zero Downtime: Data should be available 24/7 without any interruptions.
- Data Retention: It’s essential to determine how long data will be retained for future access.
- Data Disaster Recovery: Backup mechanisms should be in place in case the original database crashes or gets corrupted.
This triad is the foundation for running a business smoothly and ensuring customer satisfaction.
Read more about Data Security & Compliance
testing comment
Your place is valueble for me. Thanks!…