Cyber security is the process involves different tools & technologies to protect computer systems, networks, devices, and data from cyber-attack.
Security makes sure that none of the element in an organization is exploited to unauthorized access, to avoid any reputational, personal, and financial loss.
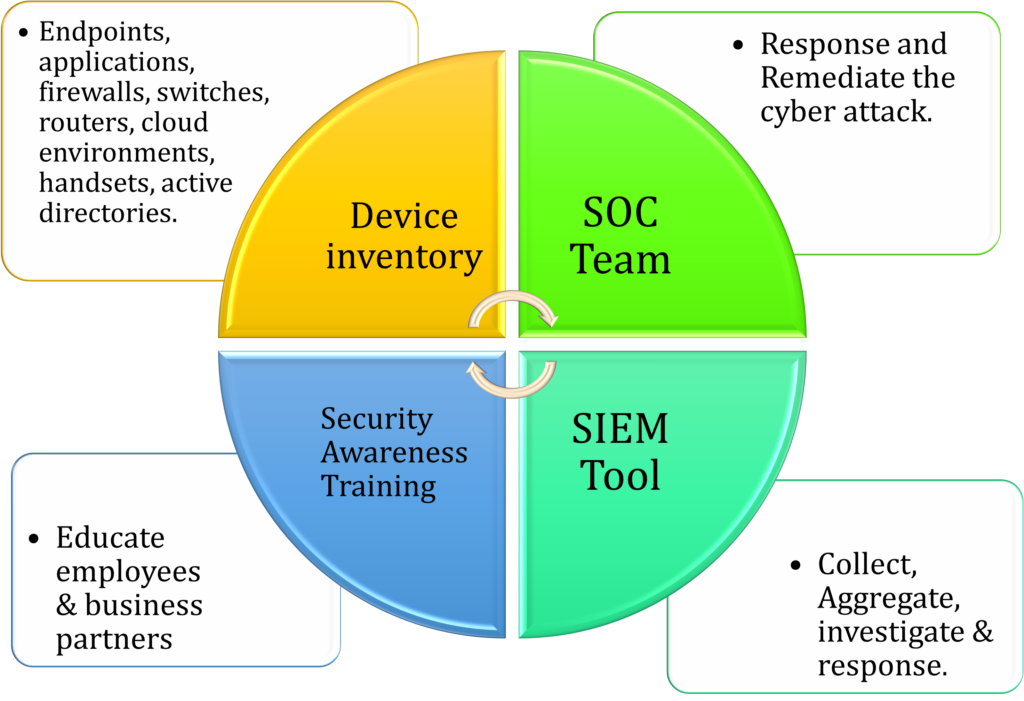
Understanding your organization computer network:
- List of devices available in your organization, also called as devices Inventory.
- Layout of computer network, physical and logical connections between devices, protocols and services use to manage them.
- Make sure that organization network should follows necessary laws, regulations, and industry standards such as GDPR, HIPPA, PCI DSS & ISO 27001.
Well trained Security Operation Center (SOC Team):
SOC team will be responsible for monitoring, detecting, analyzing, and responding to security incidents.
SOC team will proactively scan computer networks, implement some automation using different tools to find out security breaches within network.
Investigate un-trusted IP’s, Domains, URL’s and other sources and block them as early as possible.
Fully functional Security Information & Event Management (SIEM) tool:
SIEM is the software platform, where logs from all different environment is stored at one centralized location.
Once data is stored, different techniques will be applied on that stored data to scan it, detect, investigate, and respond to security threats and incidents more efficiently.
e.g.multiple login failures, malware detection, if any file changed, ssh brute force, if any registry changes detected.
Threat Intelligence (TI):
There are organizations who keeps record of tactics, techniques, and procedures (TTP’s) used by attackers, also indicators of compromises (IOC’s) associated with specific attack.
The records have list of untrusted IP’s, Domains, file hashes, URL’s, registry keys, network traffic patterns, websites, user emails, malware application names etc.
Then this list/feed of records is imported in SIEM tool andused by SOC team to see if their organization environment logs matchwith any record from Threat Intelligence feed.
If any device logs found matching with Threat Intelligence record, then SOC team will take necessary action for that device.
Security Awareness and Training:
Organization should keep weekly monthly or yearly training on common cybersecurity best practices.
Which includes how to keep own device protected from cyber attackers, what type of emails are not legitimate, which links, URL’s websites user should not open or clicked on it.
What type of attachments are risky and can install malwares on systems. Which type of applications user should not installed on their devices, etc.
Great write-up, I抦 normal visitor of one抯 web site, maintain up the nice operate, and It’s going to be a regular visitor for a long time.
It抯 exhausting to seek out knowledgeable individuals on this topic, however you sound like you recognize what you抮e speaking about! Thanks
We’re a gaggle of volunteers and opening a brand new scheme in our community. Your web site provided us with useful information to work on. You’ve performed a formidable process and our entire neighborhood can be grateful to you.
you are really a good webmaster. The web site loading speed is incredible. It seems that you are doing any unique trick. Moreover, The contents are masterwork. you have done a magnificent job on this topic!
Thanks for your feedback.
Thanks a bunch for sharing this with all of us you actually recognize what you are talking about! Bookmarked. Kindly additionally talk over with my site =). We will have a link alternate agreement between us!
Hi, Neat post. There’s an issue together with your web site in internet explorer, might check this?IE nonetheless is the market leader and a huge element of other folks will omit your wonderful writing because of this problem.
I tried loading in edge, its loading fine. I will check with IE and update. Thanks
I was just looking for this info for a while. After six hours of continuous Googling, at last I got it in your web site. I wonder what’s the lack of Google strategy that don’t rank this type of informative websites in top of the list. Generally the top sites are full of garbage.
Hello there, I discovered your blog by way of Google at the same time as looking for a related matter, your web site came up, it seems good. I have bookmarked it in my google bookmarks.
Nice blog! Is your theme custom made or did you download it from somewhere? A design like yours with a few simple adjustements would really make my blog shine. Please let me know where you got your design. Many thanks
Thanks for your feedback, I am using sparkling Theme by Colorlib Powered by WordPress.
Informative articles, excellent work site admin! If you’d like more information about Entrepreneurs, drop by my site at YH9 Cheers to creating useful content on the web!